
As a team confronting ransomware attacks on a daily basis we can confirm they are surging. However, we would take it a step further. Not only are instances of ransomware on the rise, but ransomware attacks are evolving to become even more pernicious.
Here are two examples.
Over the past 12 months, there’s been a clear trend towards “extortionware”. This modus operandi sees attackers not only demanding payment in exchange for unlocking an organisation’s data and systems. They also threaten to make public all the organisation’s data. This novel approach may be in response to more organisations understanding the need to back-up critical data, and thus being less inclined to pay a ransom if their data is encrypted by criminals.
Another worrying evolution in ransomware strategies sees payment demands being made to an organisation’s customers, in addition to the organisation itself. In September 2020, one of Finland’s largest psychiatric clinics discovered that hackers had stolen potentially tens of thousands of patients’ medical records. It is believed the breach may have started as far back as November 2018. Not only did the attackers seek a ransom from the psychiatric clinic. They also began demanding ransoms from individual patients, threatening to make public their confidential medical details if payments were not forthcoming.
Having closely analysed ransomware attack methodologies, it is possible to identify ways in which any organisation can strengthen its resilience in the face of ransomware attacks.
Why is ransomware such an issue?
Let’s face it – ransomware is an incredibly effective business model.
Most organisations, from SMEs to large, complex enterprises, can be breached by a reasonably sophisticated attacker. As with most cyber incidents, an attacker can make as many mistakes as they want, but a defender only needs to make one mistake for a breach to succeed.
As discussed above, ransomware attacks are on the rise. Whilst many organisations have strengthened their defences and now regularly backup their critical data, attackers have adapted by threatening to release the data online if the ransom isn’t paid.
This poses a very different kind of risk. Even if you are able to recover your data and systems without paying the ransom, the financial, reputational and operational risks from having your data made public could be catastrophic.
That’s why the battle against ransomware must involve your entire organisation. It is wrong to see ransomware as simply an “IT problem.” Stopping ransomware requires much more than having your IT team backup your data. It requires a whole-of-organisation approach to reduce your exposure to attacks succeeding in the first place. The focus needs to shift towards prevention rather than response.
The 7-step cyber kill-chain
When it comes to preventing ransomware attacks, it’s essential that you have an understanding of the “cyber kill-chain”, or the sequence of steps attackers usually follow.
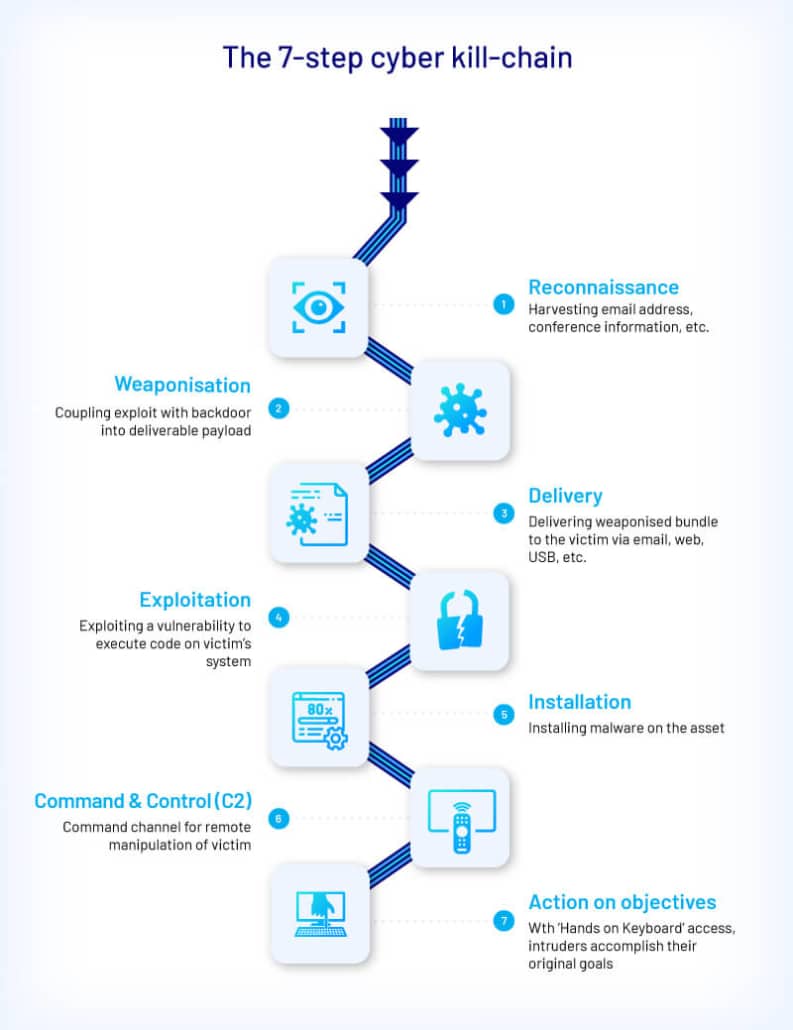
- Reconnaissance – An attacker scopes out targets to identify a potential victim.
- Weaponisation – The attacker identifies a way to breach the victim’s network.
- Delivery – An initial attack gives the attacker a foothold into the victim’s environment.
- Exploitation – The attacker may move laterally across the network, steal privileged credentials or install backdoors.
- Installation – The attacker installs malware on the asset.
- Command and Control – The attacker ensures they can remotely control the malware.
- Actions on Objectives – The attack plan is put into action.
This series of steps may be carried out in different ways, with different levels of sophistication. A less-sophisticated attacker may carry out these steps within hours. Such haste my result in mistakes, such as deleting backups, that provide opportunities for forensic investigators to identify them.
However, a more sophisticated attack will usually involve significant “dwell time” between the perimeter breach and when the ransomware attack is launched. Dwell time may extend to days, weeks or even months.
This extended dwell time assists attackers who are engaged in “Big Game Hunting.” This is an approach whereby attackers seek lucrative targets that are likely to be badly affected by ransomware, and thus more likely to pay-up. Such organisations may include those that run critical infrastructure or OT systems.
Sophisticated attacks tend to be multi-phased. The initial perimeter breach may be followed by extensive mapping activities of the network in order to gain a detailed understanding of the business operations. They may map out network users, virtual machines, host systems, connections to other networks, backup infrastructure, as well as cloud-based and on-premises platforms. These mapping activities allow them to plan their attack in a way that is designed to have the greatest operational impact, cause as much damage as possible and increase the likelihood that the victim will be forced to pay.
We recently investigated a sophisticated attack in which the attackers conducted extensive monitoring of the victim’s operations over several months from within the network perimeter. The attackers realised that the organisation was backing-up data to an external drive at a regular time each week. Knowing this information allowed them to remotely delete the backed-up data on the external drive right after the data was saved to it, but before the external drive was disconnected from the server. Following the launch of the ransomware attack, the company discovered that all the data they thought had been backed-up had actually been erased, forcing them to pay the ransom in order to recover their critical information.
What this case highlights is that ransomware attacks may be executed over a protracted period of time. Whilst an extended cyber kill-chain sequence may allow attackers to launch more sophisticated attacks, they also provide organisations more opportunities to thwart the attack. However, this will only be possible if your organisation has the appropriate prevention, detection and response systems in place.
PREVENT, DETECT, RESPOND
Attackers always looks to exploit poor security hygiene, so it’s essential you get your cyber security basics right. When it comes to mitigating the risks of ransomware, there are three broad categories of security measures you should be considering:
1. Prevent
Preventing an attack is always preferable. The security of your environment requires the involvement of your entire organisation. At a minimum you should ensure you have Multi Factor Authentication set up, particularly if members of your team have remote access. Other important considerations include:
- Patch external systems including Citrix gateways and MS remote desktop systems;
- Penetration test your external perimeter;
- Secure all ingress points;
- Disable office macros;
- “Patch your People” – Train your teams to detect and block phishing emails;
- Ensure anti-virus is set-up and configured correctly;
- Manage privileged accounts;
- Ensure Business Continuity Planning is effective;
- Prepare a response plan.
2. Detect
As highlighted previously, sophisticated ransomware attacks often involve a protracted dwell time. Whilst attackers may be mapping your network in order to launch a more devastating attack, if you’re effectively monitoring your environment you should be able to detect and intercept them. Consider the following:
- Monitor all remote access;
- Monitor key security logs;
- Monitor anti-virus;
- Monitor for phishing emails;
- Monitor other security systems;
- Properly investigate all suspicious events.
3. Respond
A prompt and effective response to a ransomware attack is crucial. With a well-tested, well-executed Business Continuity Plan in place, the impact of a ransomware attack will be significantly reduced and the consequences easier to manage. It’s essential to:
- Ensure response is properly coordinated;
- Convene response team;
- Enact response plans;
- Enact Business Continuity Plan;
- Engage experts to assist.
Until recently, the focus for both regulators and cyber security professionals has been on ensuring organisations adopt an appropriate response in the event of a breach. However, increasingly stakeholders expect organisations to have appropriate systems and policies in place to thwart attacks before they occur. That’s why “Prevent” and “Detect” are as critical as “Respond” when it comes to mitigating the risks of ransomware attacks. Stopping ransomware attacks before they can be executed will help you avoid potentially disastrous financial and reputational damage.
How can CyberCX help?
We begin by undertaking extensive investigations to obtain as much information as possible about the attack and the people behind it. Whenever possible we restore encrypted data and systems so you can avoid the need to pay.
Contact us for further advice on mitigating the risks of ransomware attacks and for assistance when you need it.






