
With so many cyber solutions available on the market, organisations need to find a way to balance prevention with detection and response capabilities. A SOC (Security Operations Centre) is a key component in realising the value of a business’ security technology investment, and provides 24/7 capability to identify and remediate potential cyber security issues in minimal time. An effective SOC will reduce the level of harm that threat actors can cause to business operations, and will identify improvements to the business’ security posture.
The decision to insource or outsource a SOC will depend on a range of considerations, but ultimately the question to answer is one of value. The following is a list of the advantages and challenges of implementing an in-house capability, as well as the benefits and caveats of outsourcing, to help weigh up which option is the best for your business.
Building an in-house SOC capability

Advantages of In-Sourcing
Fast Time to Action
An internal SOC has the advantage of a workforce who are familiar with the company’s ecosystem and the challenges that come with it. This can allow for faster time to action in solving security problems, provided the security operations team work closely with IT operations, and are clear on their role in the incident management process.
Customised solutions
In house security operations teams are free to choose and modify their own toolsets to suit their needs. This allows for a level of flexibility and agility in implementing new capability, such as workflow and technology automation. A key mistake to avoid however, is making design decisions which increase the level of engineering or key-person risks associated with maintaining a bespoke solution.
Clear lines of communication
If an attack does occur, communication within the organisation can be clearer and faster to react to the threat because the company uses its own means of internal communication. This is especially true if the organisation regularly updates, communicates, and tests its incident response plans.
Default end-to-end ownership of an incident
In the event that a cyber incident occurs, an internal SOC Team will be expected to progress the incident from its detection up to remediation. In many external SOC agreements, the provider might focus only on triaging alerts and notification of incidents that the organisation must progress themselves, which leaves the organisation with a capability gap that it must fill with an in-house team.
Challenges when In-Sourcing
Significant investment
The implementation of an internal SOC (particularly one which provides 24×7 detection and response capability) requires a significant initial and ongoing financial investment. Many organisations which eventually decide against insourcing their SOC have gone down the path of purchasing expensive security tooling, only to find that implementing, maintaining, and operating those tools can come with hidden costs such as unexpected licensing growth as more data is ingested into the SIEM, maintenance and engineering costs, specialist training courses, and overtime allowances for operational staff.
Recruitment, training and retention
A SOC requires a team of experts in multiple areas, such as security tools engineering, security use case creation, event analysis and triage, incident response and forensics investigations, cyber intelligence, and threat hunting. It can take significant time to recruit, and significant budget to train a team with expert knowledge of the technologies and processes required to perform effective security operations.
Added to this, the talent pool from which to recruit SOC analysts and cyber security experts is limited. This makes an in-house SOC more vulnerable to the effects of staff churn, such as losing key organisational knowledge. An in-house SOC team might consist of as few as 4 staff, losing two staff members in quick succession places pressure on the business to maintain visibility over security alerts, let alone devote time to active threat hunting.
Getting to (and maintaining) value
Setting up and fine-tuning security tools can take months or even years to reach full maturity, especially when starting a SOC capability from scratch. A common complaint of organisations that are reconsidering their decision to insource their SOC is their realisation that they are not getting the most out of their investment in tooling. While an organisations’ staff may be drowning in false positive security alerts, they may not have enough spare time (or operational expertise) to devote to creating new security use cases and detections that keep pace with cyber attackers.
Distraction from core business objectives
The SOC team, like any high performing business unit, requires continued management focus on top of the significant financial investment. Many organisations have found that insourced SOC teams can become a distraction to running the business, as they compete with other key technology or digital transformation initiatives for management time and attention. This can even limit the focus available for executing upon core business objectives.
Reinventing the wheel
Insourced SOCs are often forced to prioritise getting to a baseline level of operational maturity over taking time to document operational processes and procedures. The risk is that business knowledge can be lost in the event of staff departure, with updates to documentation also forgotten. In comparison, an MSS provider can leverage playbooks, processes, and procedures developed by a larger team across many client environments. This is one of the foundations of operating at the scale an MSSP usually operates at.
“Building a SOC or buying a SOC have got their own advantages and disadvantages. Without a shadow of a doubt employing a credible MSS provider proves to be quicker, more cost effective and allows business leaders to focus on their core business objectives. The most important thing though is the awareness that, in the current threat landscape, having cyber security protection in place is not an ‘option’ but a ‘must’ unless the organisation is prepared to accept the risk and deal with the potential consequences of not having it in place.”
Seb Krupowicz, UK SOC Manager, CyberCX
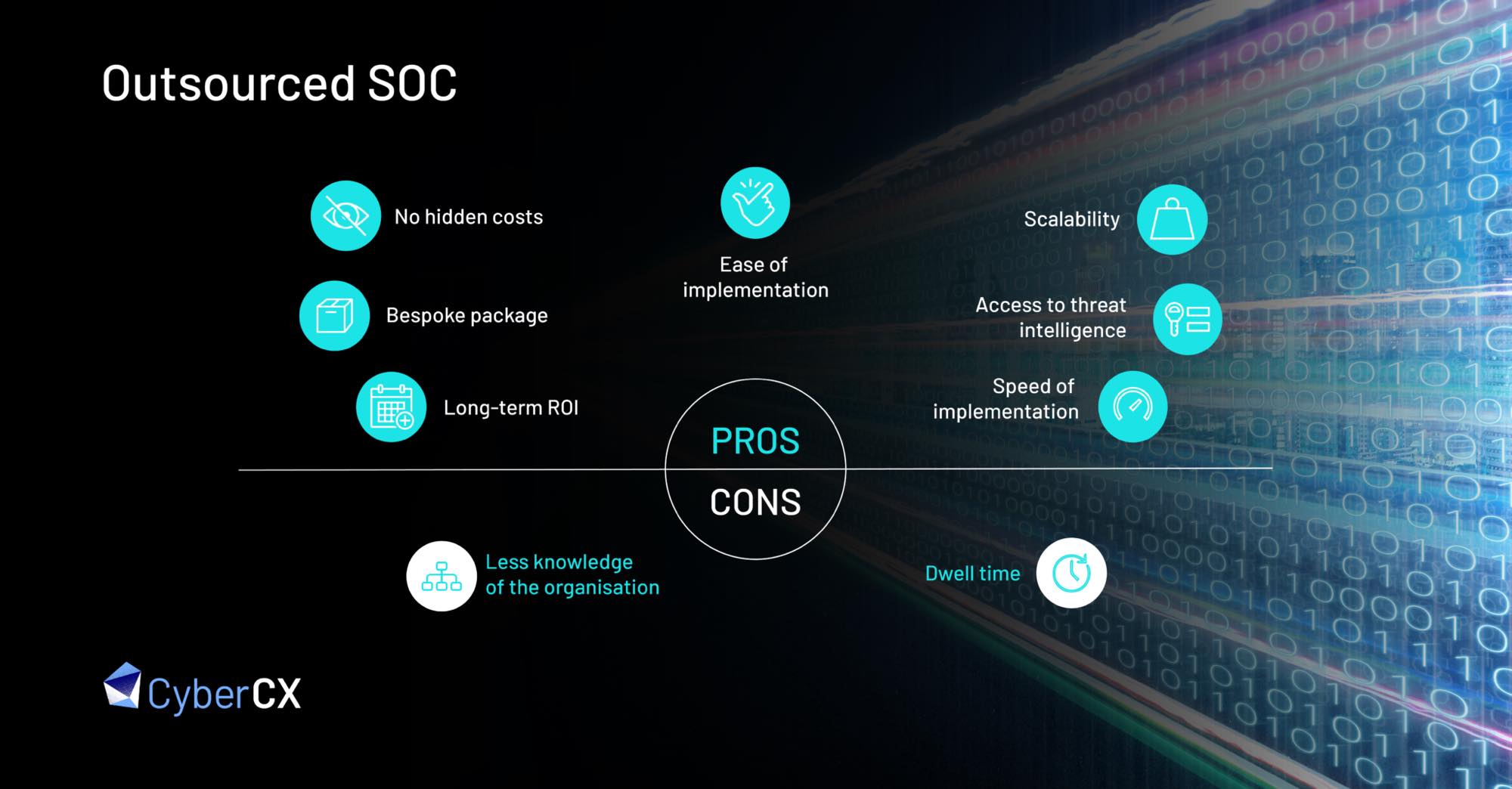
Outsourced SOC
For many organisations, an outsourced Security Operation Centre can be a more cost-effective solution. Partnering with the right provider gives an organisation many of the pros of an in-sourced SOC, whilst avoiding all of the challenges outlined above. However, it is important to select a provider with a proven track record of implementing and delivering SOC services, utilising best of breed security technologies.
“Knowing there is a team of specialists who look after our security operations gives us the confidence to carry out our day job and sleep peacefully at night.”
Craig Flanagan Senior ICT Services Manager
Benefits
Access to immediate expertise
Onboarding an external SOC provider avoids the complexity of implementing a SOC capability from scratch. Partnering with the right provider will give the organisation immediate access to operational and technical expertise, with the ability to implement, configure, and maintain the tools required to detect and respond to cyber threats.
Ease and speed of implementation
A mature SOC provider will bring their existing playbooks, processes, and procedures, allowing analysts to spend more time triaging, threat hunting, and staying abreast of current trends and activities associated with sophisticated threat actors.
This can be a game-changer for the organisation. In many cases, the transition from no or very limited protection to having a fully-fledged and mature SOC can be done within weeks as opposed to months, or in some cases, years.
Scalability
An outsourced SOC arrangement using a leveraged model or a pool of security analysts and engineers servicing multiple clients, means that as client organisations grow, they can take advantage of the spare capacity in the SOC. This allows for rapid scalability in size and scope of services as organisational needs change over time.
Access to threat intelligence
There are many open source and third party subscription based threat intelligence feeds and finished intelligence available to in-house SOC teams which provide access to indicators of compromise (IOCs) that can be fed directly into security tools. One advantage of choosing a third party SOC provider however, particularly a large and established operator, is their access to ‘first party’ threat intelligence. A SOC provider with multiple customers across a range of industries and geographic regions will have greater visibility of actions and trends associated with a range of threat actors. Furthermore, providers that perform end-to-end major incident response and digital forensics are the first to obtain real world IOCs and tactics, techniques and procedures (TTPs) which, when automatically fed into a customer organisation’s SIEM and EDR platforms, can provide instantaneous threat coverage across real world threat actor activities.
Risk reduction
A mature SOC provider will continuously invest in cutting edge tools, automation, and skilling up its analysts. This avoids the risks associated with technology debt, as well as key personnel risks.
Long-term ROI and cost transparency
Outsourcing the SOC can reduce the number of operational security personnel a company needs to hire. This is particularly the case if the MSSP utilises a leveraged model, allowing them to time slice effort for client organisations across different specialist roles such as security operations analyst, platform engineer, cyber intelligence analyst, threat hunting specialist, digital forensics expert, and incident responder. When coupled with a clearly articulated contract and statement of work, this means a reduction in overall staff costs and access to a wider range of skills, all whilst avoiding the hidden costs associated with insourcing.
What to look for in an external SOC provider
- A proven methodology to onboard the service
- The provider uses best of breed technologies (be careful of providers that utilise open source software to save cost)
- Contract scope is unambiguous
- Clear delineation of roles and responsibilities between the organisation’s internal teams and SOC staff
- Look for a leveraged model
How can CyberCX help?
If you want to find out more about outsourcing your SOC via an MSSP, get in touch with one of our experts today.






